Finding and Fixing a Simple IDOR on the Avatao Challenge
Finding and Fixing a Simple IDOR on the Avatao Challenge
I came across a challenge on the avatao.com site. Very simple IDOR. The site has a couple of challenges and this was my first attempt at these online challenges i never do.
The challenge addresses a brocken Access Control issue. Challenges are very similar to the portswigger academy labs. Let’s dive in.
Walkthrough
- After accessing the link, i started the exercise.
- Click webservice to start the lab in a new tab

- Register on the portal and log in using the new credentials.
- The goal is to find the nickname of a suspicious user. The profile endpoint shows my id as 20 (id=20)
1
/webservice/profile?id=20
- Using burp intruder, we can fuzz from 1 through 30, revealing the user id 19 details.
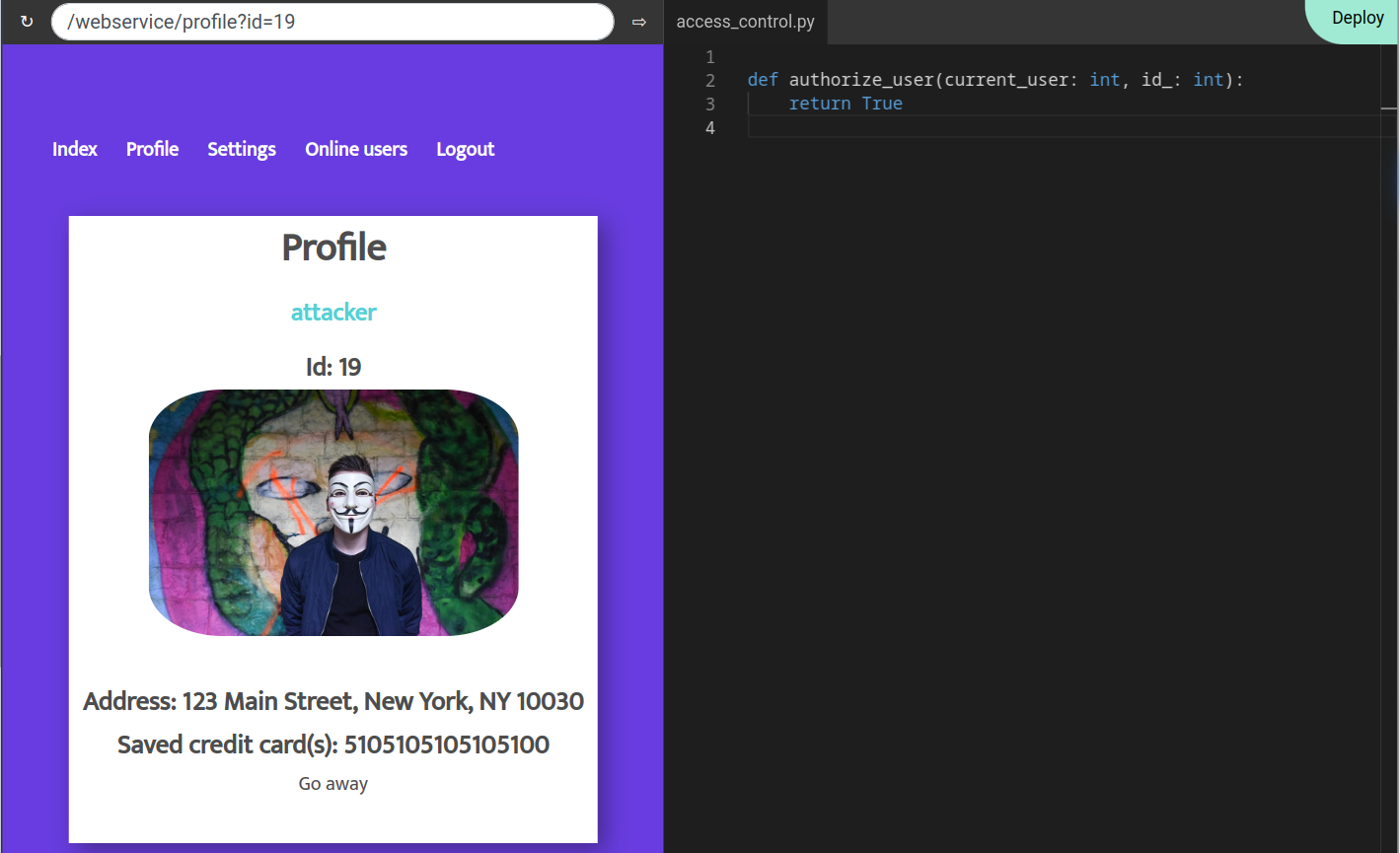
- The next challenge was to fix this IDOR. We have the following python code, access_control.py that handles this logic.
1 2
def authorize_user(current_user: int, id_: int): return True
- The function should return
Trueif theid_parameter matches thecurrent_userparameter (the ID of the user who sent the request). Both parameters are integers. - This can be done using a simple if statement. If the
current_userandid_match, it will returnTrue, henseFalse.1 2 3 4 5 6
def authorize_user(current_user: int, id_: int): # we add this code to perform a check to match current_user to the entered id. if current_user == id_: return True else: return False
- Click on
deployto save configuration and restart the server.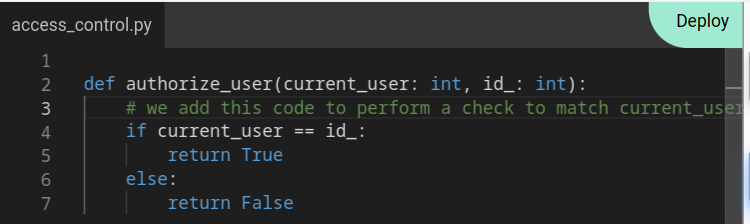
- Now visit the suspicious user’s profile
/webservice/profile?id=19and see theAuthorization error.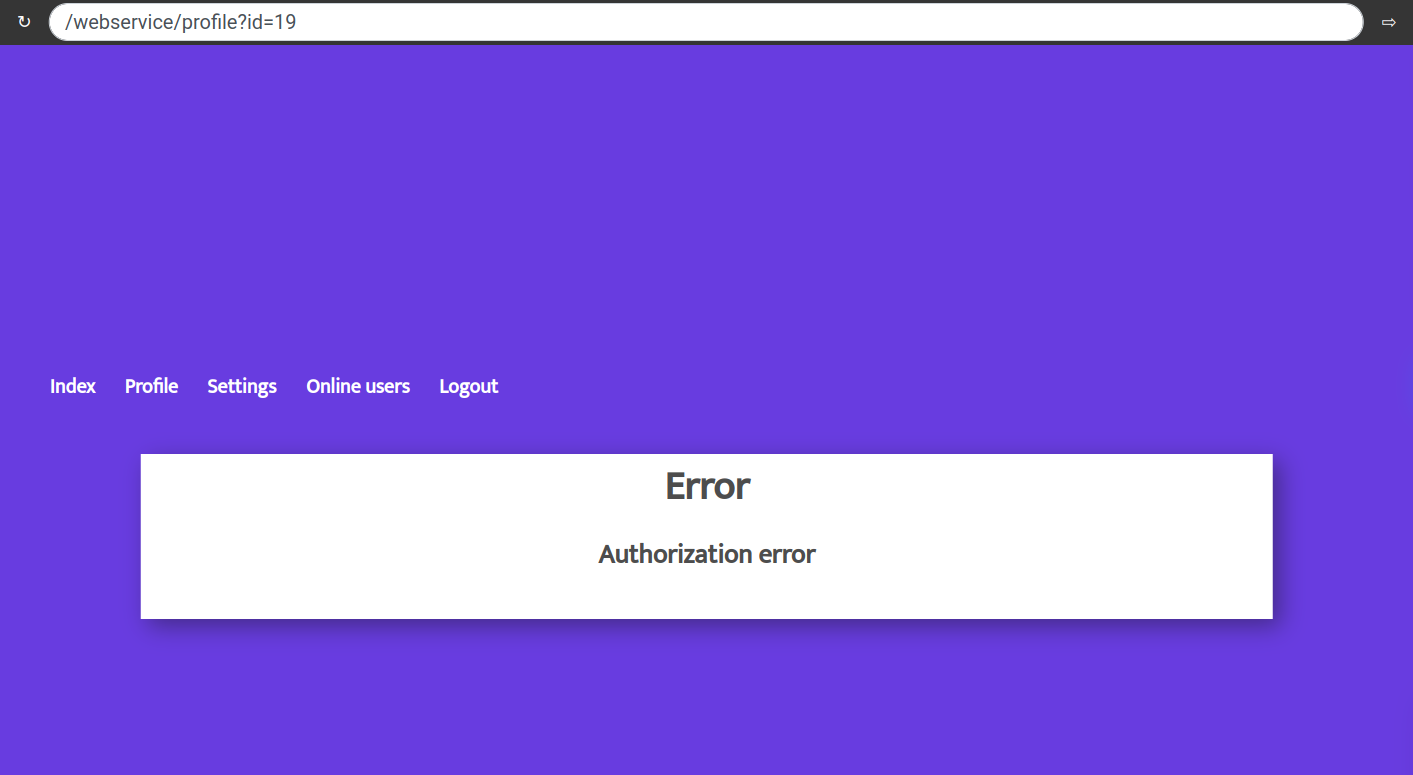 There. We fixed this at the basic level using a simple check.
There. We fixed this at the basic level using a simple check.
This post is licensed under CC BY 4.0 by the author.
